That is an opinion editorial by Scott Sullivan.
Usually Bitcoiners don’t care an excessive amount of about what goes on in Shitcoin-land, however now that Ethereum has merged to proof-of-stake (PoS), there’s been fairly the excitement on Bitcoin Twitter. After all, the Bitcoin community itself will stay unaffected, however I feel this “improve” remains to be price paying some consideration to. Now that Ethereum has cleansed itself of the “soiled” and “wasteful” externalities related to proof-of-work (PoW), we will count on the gloves to return off within the narrative warfare, and I feel Bitcoiners ought to be able to punch again.
Studying how PoS works is a very good method to internalize the variations and trade-offs between PoW and PoS. Although I had seen all of the high-level arguments in opposition to PoS earlier than — that PoS is extra permissioned, centralizing, and oligarchical — I’ll admit that with out wanting into the main points, all of it felt type of hand-wavy. By really diving into the PoS algorithm, we will start to see how all these properties naturally emerge from first ideas. So in the event you’re interested by how the PoS algorithm works, and why it results in these sorts of properties, then learn on!
Fixing The Double-Spend Drawback
Let’s begin with a fast recap of the issue we’re attempting to unravel. Suppose we’ve got a big group of individuals in a cryptocurrency community attempting to take care of a decentralized ledger. Right here’s the issue: How can new transactions be added to everybody’s ledger, such that everybody agrees on which new transactions are “appropriate”? PoW solves this downside fairly elegantly: Transactions are grouped collectively in blocks, whereby every block takes a considerable amount of computational work to provide. The quantity of labor required can transfer up or down to make sure blocks are produced each ten minutes on common, giving every new block loads of time to propagate all through the community earlier than the following one is created. Any ambiguity is resolved by deciding on the chain with probably the most work, and double-spending is prevented as a consequence of requiring at the very least 51% of the worldwide hashpower for a double-spend block to catch up.
However suppose now we wish to throw away Satoshi Nakamoto’s key perception that made all of this potential within the first place. In spite of everything, these pesky ASICs are loud and annoying, they usually eat extra power than all of George Soros, Invoice Gates and Hillary Clinton’s personal jets mixed. Is there a way we will unambiguously agree on which transactions are true simply by speaking it out?
Ethereum’s proof-of-stake proposes to unravel this downside utilizing two key elements. The primary is to make particular “checkpoint blocks” every so often, whose objective is to present assurance to everybody within the community concerning the “reality” of the system at numerous deadlines. Making a checkpoint requires a two-thirds majority vote by stake, so there’s some assurance that almost all of validators agreed on what the reality really was at that time limit. The second ingredient is to punish customers for including ambiguity to the community, a course of generally known as “slashing.” For instance, if a validator have been to create a fork, or vote on an older sidechain (much like a 51% assault), then their stake would get slashed. Validators will also be slashed for inactivity, however not as a lot.
This leads us to our first precept behind PoS, which is that PoS relies on a adverse (penalty-based) incentive system.
This contrasts closely with Bitcoin and proof-of-work, which is a constructive (reward-based) incentive system. In Bitcoin, miners can try to interrupt the principles — badly formatted blocks, invalid transactions, and so forth — however these blocks will simply get ignored by full nodes. The worst-case situation is a little bit of wasted power. Miners are additionally free to construct on older blocks, however with out 51% of the hashpower, these chains won’t ever catch up, once more simply losing power. Any miner who participates in these actions, whether or not deliberately or not, needn’t fear about dropping their accrued bitcoin or mining machines, however they gained’t get new rewards. Quite than reside in worry, bitcoin miners can err on the facet of taking motion and danger.
The world is a really completely different place for validators residing in Ethereum-land. As a substitute of working exhausting and being rewarded for including safety to the community, validators do no precise work, however have to be cautious that their node by no means misbehaves, lest they watch their financial savings go up in flames. If any proposed modifications have been made to the community, a validator’s first intuition could be to adjust to no matter everybody else was doing, or else danger getting slashed. To be a validator is like strolling on eggshells on a regular basis.
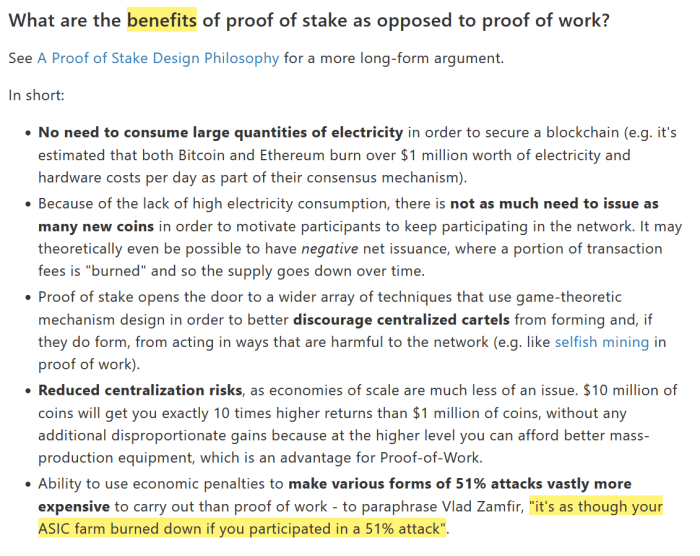
By the best way, residing underneath a adverse incentive system is among the, ahem, “advantages” of proof-of-stake, in response to the Ethereum community’s co-founder Vitalik Buterin’s FAQ:
So how would slashing really work on a technical stage? Wouldn’t we have to first create an inventory of all of the validators, with a view to have one thing to slash within the first place? The reply is sure. To develop into a validator in Ethereum, one should first transfer ETH right into a particular “staking” tackle. Not solely is that this record wanted for slashing, but in addition for voting since a two-thirds majority vote is required for checkpoint blocks.
There are some attention-grabbing implications to sustaining an inventory of all validators always. How exhausting is it to affix? How exhausting is it to go away? Do validators get to vote on the standing of different validators?
This brings us to our second precept behind PoS, which is that PoS is a permissioned system.
Step one in changing into a validator is to deposit some ETH right into a particular staking tackle. How a lot ETH? The minimal required is 32 ETH, or about $50,000 on the time of this writing. For context, an honest bitcoin mining rig usually runs within the single-digit 1000’s of {dollars}, and a house miner can begin with a single S9 for a number of hundred bucks. To be honest, ETH’s excessive entry charge has a technical justification, since the next stake means fewer validators, which lowers bandwidth.
So the deposit charge is excessive, however at the very least anybody who owns 32 ETH is free to affix or depart at any time, proper? Not fairly. There are safety dangers if giant coalitions of validators have been to all enter or exit on the similar time. For instance, if a majority of the community all left without delay, then they may double-spend a finalized block by replaying a fork by which they by no means left, with out getting slashed on both chain. To mitigate this danger, the on- and off-ramps have a built-in throughput restrict. At present this restrict is about to max(4,|V|/65536) validators per epoch (each 6.4 minutes), and is similar for each getting into and leaving. This interprets roughly to 1 full validator set each ten months.
By the best way, despite the fact that it’s at present potential for validators to publish an “exit” transaction and cease validating, the code to really withdraw funds hasn’t even been written but. Sounds a bit like “Lodge California” …
There’s one final level concerning the incentives behind approving new validators. Suppose you have been a shareholder in a big and steady firm paying common dividends each quarter. Would it not make sense to present new shares away without cost? After all not, since doing so would dilute the dividends of all present shareholders. An analogous incentive construction exists in PoS, since every new validator dilutes the income of all present validators.
In concept, validators might merely censor each single transaction that provides a brand new validator; nevertheless, in observe, I feel such a blunt strategy could be unlikely. This may be very noticeable and would destroy Ethereum’s picture of “decentralization” in a single day, doubtlessly crashing the worth. I feel a extra refined strategy could be used as a substitute. For instance, the principles might slowly change over time making it more durable to develop into a validator, with excuses being supplied equivalent to “safety” or “effectivity.” Any insurance policies that enrich present validators on the expense of latest validators would have monetary tailwinds, whether or not spoken out loud or not. We will begin to see why PoS would have a tendency in direction of oligarchy.
Overview Of The Casper Algorithm
Now that we all know the high-level technique behind PoS, how does the algorithm really work? The primary concepts behind checkpoints and slashing have been put ahead in an algorithm known as Casper, so we’ll begin there. Casper itself doesn’t really specify something about the way to produce blocks, however relatively offers a framework for the way to superimpose a checkpoint/slashing technique on prime of some already-existing blockchain tree.
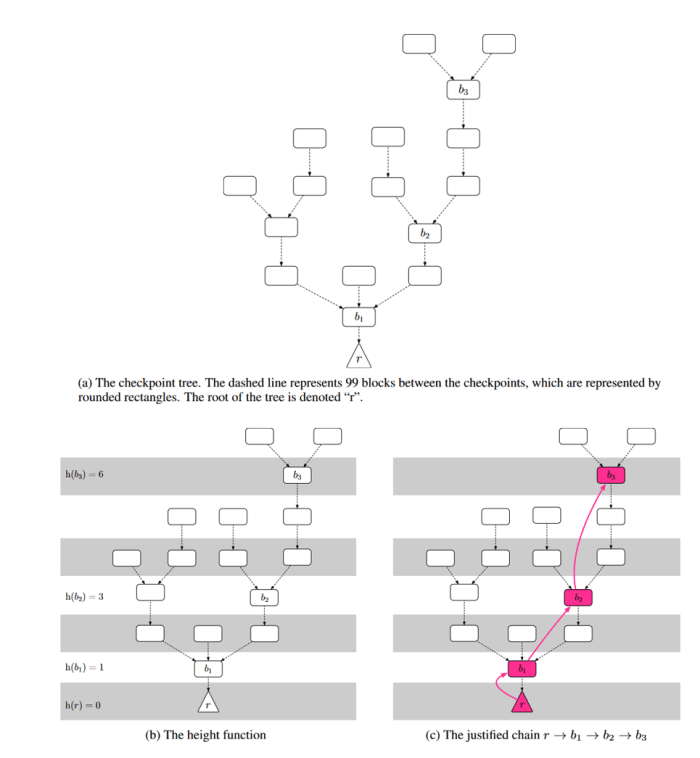
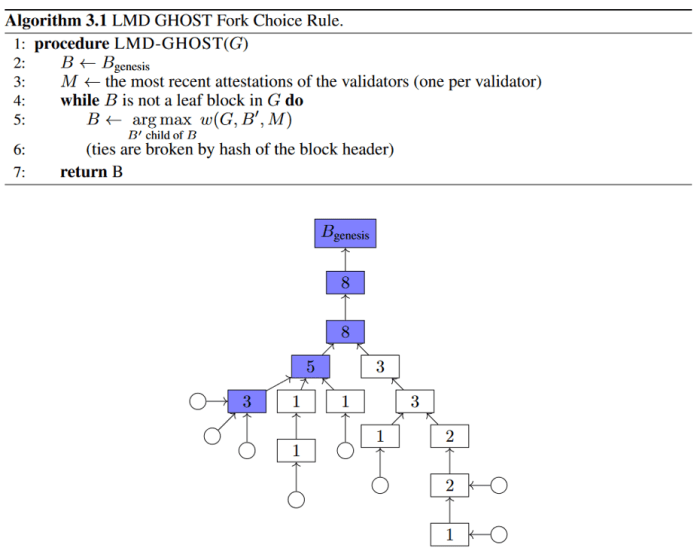
First, some arbitrary fixed (C) is chosen to be the “checkpoint spacing” quantity, which determines what number of blocks happen between checkpoints; for instance, if C=100 then checkpoints would happen at blocks 0, 100, 200, and so forth. Then the nodes all vote on which checkpoint block ought to be the following “justified” checkpoint. Quite than vote on single blocks in isolation, validators really vote on (s,t) checkpoint pairs, which hyperlink some beforehand justified checkpoint supply “s” to some new goal checkpoint “t.” As soon as a checkpoint hyperlink (s,t) will get a two-thirds majority vote by stake, then “t” turns into a brand new justified checkpoint. The diagram under exhibits an instance tree of checkpoints:
On this diagram, the h(b) perform is referring to the “checkpoint top,” e.g., the block’s a number of of 100. You might have seen that not each hundredth block is essentially justified, which might occur if the vote failed at a sure top. For instance, suppose at top 200 two separate checkpoints every obtained 50% of the vote. Since voting twice is a slashable offense, the system would get “caught” except some validators willingly slashed their very own stake to realize a two-thirds vote. The answer could be for everybody to “skip” checkpoint 200 and “strive once more” at block 300.
Simply because a checkpoint is justified, doesn’t imply it’s finalized. To ensure that a checkpoint to rely as finalized, it have to be instantly adopted by one other justified checkpoint on the subsequent potential top. For instance, if checkpoints 0, 200, 400, 500 and 700 have been all justified and linked collectively, solely checkpoint 400 would rely as “finalized,” since it’s the just one instantly adopted by one other justified checkpoint.
As a result of the terminology may be very exact, let’s recap our three classes. A “checkpoint” is any block which happens at top C*n, so if C=100, each block with top 0, 100, 200, 300, and so forth would all be checkpoints. Even when a number of blocks have been created at top 200, they might each be “checkpoints.” A checkpoint is then “justified” if it’s both the basis block at top 0, or if two-thirds of the validators voted to create a hyperlink between some beforehand justified checkpoint and the present checkpoint. A justified checkpoint is then “finalized” if it then hyperlinks to a different justified checkpoint on the subsequent potential top. Not each checkpoint essentially turns into justified and never each justified checkpoint essentially turns into finalized, even within the remaining chain.
Casper Slashing Guidelines
The slashing guidelines in Casper are designed such that it’s unimaginable for 2 finalized checkpoints to exist in two separate forks, except at the very least one-third of the validators broke the slashing guidelines.
In different phrases, solely finalized checkpoints ought to ever be counted as unambiguous “reality” blocks. It’s even potential for 2 justified checkpoints to happen on either side of a fork, simply not two finalized checkpoints. There’s additionally no assure about when or the place the following finalized checkpoint will happen, simply that if a series break up have been to happen, then you need to sit again and wait till a finalized block exhibits up someplace, and as soon as it does then you recognize that’s the “appropriate” chain.
There are two slashing guidelines in Casper which implement this property:
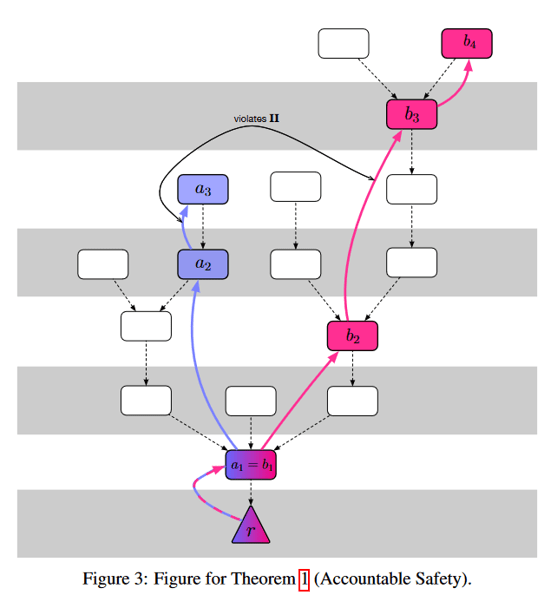
The primary rule forbids anybody from double-voting on checkpoints with the identical goal top, so if a validator voted for 2 completely different checkpoint blocks with goal top 200, that will be a slashable offense. The aim of this rule is to stop the chain from splitting into two completely different justified checkpoints with the identical top, since this could require 2/3 + 2/3 = 4/3 of the entire validator votes, implying that at the very least one-third of the validators broke the slashing guidelines. Nonetheless, as we noticed beforehand, it’s potential for justified checkpoints to “skip” sure block heights. What prevents a series from splitting into completely different goal heights? For instance, couldn’t checkpoint 200 fork into justified checkpoints at 300 and 400 with out anybody getting slashed?
That’s the place the second rule is available in, which mainly prevents validators from “sandwiching” votes inside different votes. For instance, if a validator voted for each 300→500 and 200→700, that will be a slashable offense. Within the case of a series break up, as soon as one department sees a finalized checkpoint, it turns into unimaginable for the opposite department to see a justified checkpoint afterwards except at the very least one-third of the validators broke rule #2.
To see why, suppose the blockchain forked into justified checkpoints 500→800 and 500→900, then sooner or later the primary chain noticed a finalized checkpoint with hyperlink 1700→1800. Since each 1700 and 1800 can solely be justified on fork #1 (assuming no one broke the primary slashing rule), the one method fork #2 might see a justified checkpoint after 1800 is that if there was some voted-in hyperlink between heights H<1700 and H>1800. However since this vote would “sandwich” the 1700→1800 hyperlink and require a two-thirds vote, and the 1700→1800 already handed with a two-thirds vote, then at the very least one-third of the validators would wish to interrupt rule #2. The Casper paper has a pleasant diagram demonstrating this property:
And that’s it, simply observe the Casper guidelines and also you’re good!
Appears fairly easy, proper? I’m positive PoS would solely ever use slashing as an absolute final resort to take care of consensus, and never as an extortionary mechanism to stress validators into behaving a sure method … proper?
(Source)
This brings us to our third precept behind PoS: There are not any guidelines. The “guidelines” are no matter everybody else says they’re.
At some point your node may very well be technically following each Casper commandment to the letter, and the following day your financial savings may very well be slashed since you have been doing one thing everybody else didn’t like. Authorized a “staff crimson” transaction that one time? Tomorrow the “staff blue” majority would possibly slash you. Or possibly you probably did the other and omitted too many “staff crimson” transactions? Tomorrow the “staff crimson” majority would possibly slash you for censorship. The power to slash goes far past the restricted scope of OFAC (Workplace of Overseas Belongings Management) censorship. PoS is sort of a nonstop Mexican standoff, the place the implicit menace of slashing is ever-present always.
I wouldn’t be shocked if in a contentious exhausting fork, either side hard-coded the validation guidelines of the opposite fork, simply in case they needed to punish anybody who joined the “mistaken” facet. After all, this could be a nuclear possibility, and like nukes, all sides would possibly solely select to strike in retaliation. I might guess that the majority particular person validators are impartial in that they might prioritize monetary self-preservation over political self-sacrifice, however would possibly outwardly take a facet in the event that they sensed that was the proper transfer to keep away from getting slashed.
What Time Is It?
Now that we all know the fundamentals of checkpoints and slashing, we will transfer onto the precise algorithm utilized in Ethereum, known as Gasper. It is a portmanteau of Casper, which we’ve already coated, and GHOST, a method for choosing the “finest” chain of blocks in between checkpoints.
The very first thing to grasp about Gasper is that point itself is the principle unbiased variable. Actual-world time is split into twelve-second items known as “slots,” the place every slot accommodates at most one block. These slots then kind bigger teams known as “epochs,” the place every epoch refers to 1 checkpoint. Every epoch accommodates 32 slots, making them 6.4 minutes lengthy.
It’s price noting that this paradigm flips the causal relation between time and block manufacturing when in comparison with PoW. In PoW, blocks are produced as a result of a legitimate hash was discovered, not as a result of sufficient time had handed. However in Gasper, blocks are produced as a result of sufficient real-world time has handed to get to the following slot. I can solely think about the tough timing bugs such a system could encounter, particularly when it’s not only one program working on one laptop, however tens of 1000’s of computer systems attempting to run in sync everywhere in the world. Hopefully, the Ethereum builders are aware of the falsehoods programmers imagine about time.
Now suppose you have been beginning up a validator node, and also you have been syncing the blockchain for the primary time. Simply since you noticed that sure blocks referenced sure timestamps, how might you make sure that these blocks have been actually produced at these occasions? Since block manufacturing doesn’t require any work, couldn’t a malicious group of validators simulate a completely pretend blockchain from day one? And in the event you noticed two competing blockchains, how would you recognize which is true?
This brings us to our fourth precept behind PoS, which is that PoS depends on subjective reality.
There’s merely no goal method to decide between two competing blockchains, and any new nodes to the community should in the end belief some present supply of reality to resolve any ambiguity. This contrasts considerably with Bitcoin, the place the “true” chain is all the time the one with probably the most work. It doesn’t matter if a thousand nodes are telling you chain X, if a single node broadcasts chain Y and it accommodates extra work, then Y is the proper blockchain. A block’s header can show its personal price, utterly eradicating the necessity for belief.
By counting on subjective reality, PoS reintroduces the necessity for belief. Now I’ll admit, I’m maybe barely biased, so if you wish to learn the opposite facet, Buterin wrote an essay containing his views right here. I’ll admit that in observe, a series break up doesn’t appear all that probably given the Casper guidelines, however regardless, I do get some peace of thoughts figuring out that this isn’t even a risk in Bitcoin.
Block Manufacturing And Voting
Now that we’re aware of slots and epochs, how are particular person blocks produced and voted on? Initially of every epoch, the complete validator set is “randomly” partitioned into 32 teams, one for every slot. Throughout every slot, one validator is “randomly” chosen to be the block producer, whereas the others are chosen to be the voters (or “attestors”). I’m placing “randomly” in quotes as a result of the method have to be deterministic, since everybody should unambiguously agree on the identical validator units. Nonetheless this course of should even be non-exploitable, since being the block producer is a extremely privileged place because of the additional rewards out there from miner extractable worth (MEV), or because it’s being renamed, “most extractable worth.” “Ethereum Is A Darkish Forest” is a good learn on this.
As soon as a block is produced, how do the opposite validators vote or “attest” to it? Block proposal is meant to occur inside the first half (six seconds) of a slot, and testifying inside the second half, so in concept there ought to be sufficient time for the attestors to vote on their slot’s block. However what occurs if the block proposer is offline or fails to speak or builds on a nasty block? The job of an attestor just isn’t essentially to vote on that slot’s block, however relatively whichever block “seems one of the best” from their view at that time limit. Beneath regular circumstances this may normally be the block from that slot, however may be an older block if one thing went mistaken. However what does “look one of the best” imply, technically? That is the place the GHOST algorithm is available in.
GHOST stands for “Greediest Heaviest Noticed SubTree” and is a grasping recursive algorithm for locating the block with probably the most “latest exercise.” Principally, this algorithm seems in any respect the latest blocks within the type of a tree, and walks down the tree by greedily deciding on the department with probably the most cumulative attestations on that complete subbranch. Solely the latest attestation of every validator counts in direction of this sum, and finally this course of lands on some leaf block.
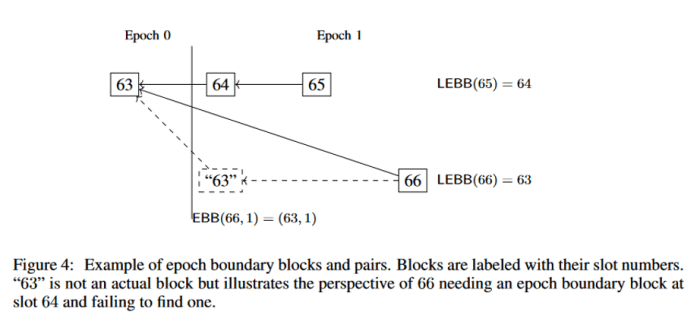
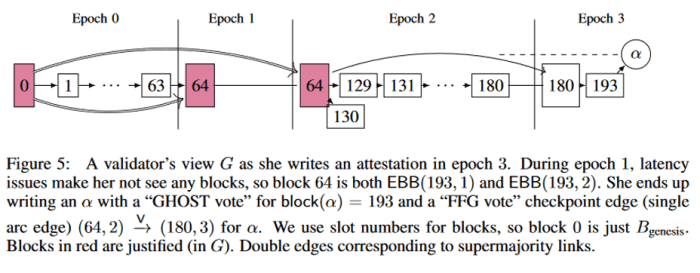
Attestations usually are not simply votes for the present finest block, but in addition the for the latest checkpoint which result in that block. It’s price noting in Gasper, checkpoints are based mostly on epochs relatively than block heights. Every epoch refers to precisely one checkpoint block, which is both the block in that epoch’s first slot, or if that slot was skipped, then the latest block earlier than that slot. The identical block can theoretically be a checkpoint in two completely different epochs if an epoch one way or the other skipped each single slot, so checkpoints are represented utilizing (epoch, block) pairs. Within the diagram under, EBB stands for “epoch boundary block” and represents the checkpoint for a selected epoch, whereas “LEBB” stands for “final epoch boundary block” and represents the latest checkpoint general.
Much like Casper, a checkpoint turns into justified as soon as the entire variety of attestations passes the two-thirds threshold, and finalized if it was instantly adopted by one other justified checkpoint within the subsequent epoch. An instance of how this voting works is proven under:
There are two slashing circumstances in Gasper, that are analogous to the slashing guidelines in Casper:
- No voting twice in the identical epoch.
- No vote can include epoch checkpoints which “sandwich” one other vote’s epoch checkpoints.
Regardless of being based mostly on epochs as a substitute of block heights, the Casper guidelines nonetheless make sure that no two finalized checkpoints can happen on completely different chains except one-third of the validators may very well be slashed.
It’s additionally price noting that attestations are included within the blocks themselves. Much like how a block in PoW justifies itself utilizing its hash, a finalized checkpoint in PoS justifies itself utilizing all of its previous attestations. When somebody does break the slashing guidelines, these unhealthy attestations are included in a block which proves the violation. There’s additionally a small reward for the block producer who included the violation, with a view to present an incentive to punish rulebreakers.
Forks
It’s attention-grabbing to consider what would occur within the case of a fork. To rapidly recap, a fork refers to a change within the consensus guidelines, they usually are available in two varieties: exhausting forks and gentle forks. In a tough fork, the brand new guidelines usually are not backwards-compatible, doubtlessly leading to two competing blockchains if not everybody switches over. In a gentle fork, the brand new guidelines are extra restrictive than the outdated guidelines, whereas holding them backwards-compatible. As soon as over 50% of the miners or validators begin imposing the brand new guidelines, the consensus mechanism switches over with out splitting the chain. Gentle forks are typically related to upgrades and new transaction varieties, however additionally they technically embody any sort of censorship enforced by a 51% majority. PoS additionally has a 3rd sort of “fork” not current in PoW: a series break up with none modifications to the principles. However since we’ve already coated this, we’ll deal with exhausting and gentle forks.
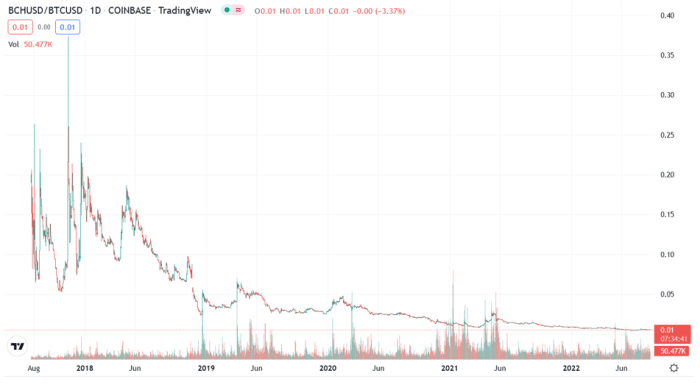
Let’s begin with the best case: a standalone contentious exhausting fork. By contentious, I imply a rule change that divides the customers politically. A bug repair or minor technical change probably wouldn’t be contentious, however one thing like altering the validation reward most likely could be. If a tough fork was contentious sufficient, it might lead to a series break up and would get resolved economically by customers promoting one chain and shopping for the opposite. This may be much like the Bitcoin Money break up in 2017, which appears to have a transparent winner:
Now suppose the validators have been sitting round at some point and determined they weren’t getting paid sufficient, and determined they need to elevate their rewards from 5% per 12 months to 10% per 12 months. This may be a transparent trade-off in favor of the validators on the expense of non-validators who would now be getting extra diluted. Within the occasion of a series break up, which chain would win?
This results in our fifth precept of PoS, which is that cash is energy.
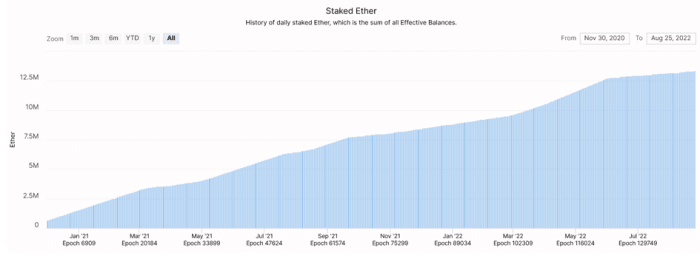
Out of the 120M ETH in existence, over 10% of that’s at present being staked, as seen within the chart under:
Given a contentious exhausting fork between the validators and non-validators, assuming that every one the non-validators market-sold the brand new chain and all of the validators market-sold the outdated chain, then in concept the outdated chain would win, for the reason that majority of ETH would nonetheless held by non-validators (90% versus 10%). However there’s a number of extra issues to contemplate. First, after any chain break up, the validators would nonetheless be “in management” of each blockchains. If the validators have been capable of affect the opposite chain, they is likely to be incentivized to make it fail. Second, there’s additionally the nuclear possibility mentioned earlier, whereby the brand new chain would possibly slash anybody nonetheless validating the outdated chain to stress them into becoming a member of. Lastly, the validators would probably carry important social and political affect over everybody else within the community. If Buterin, the Ethereum Basis and the exchanges all determined in unison they have been going to boost the staking reward, I discover it tough to imagine that common Ethereum customers and validators might hold the outdated fork going whereas additionally making it extra worthwhile by shopping for stress.
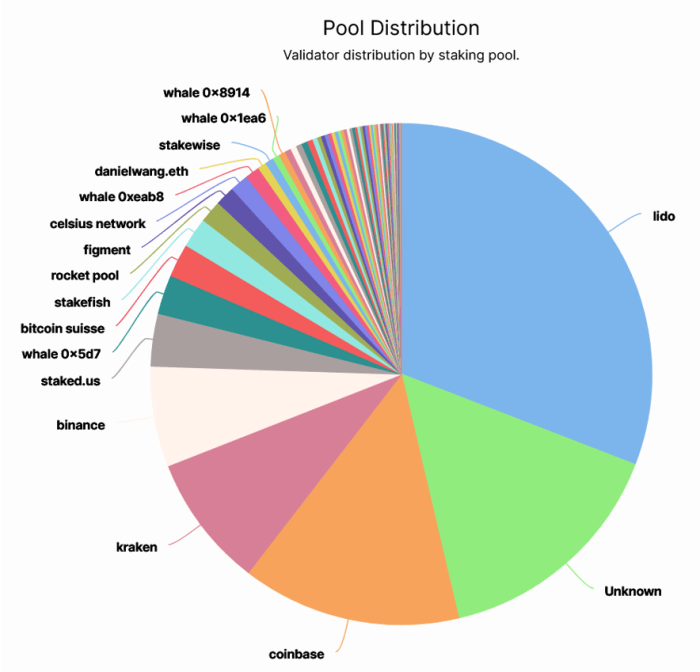
Transferring on to gentle forks, what would occur in a contentious gentle fork, equivalent to OFAC censorship? The validators are pretty centralized, as we will see within the chart under:
Not like PoW the place miners can change swimming pools on the press of a button, validators in Ethereum are locked right into a staking tackle till they course of an exit transaction. If Lido and the highest exchanges have been made to censor sure transactions, they may simply cross the two-thirds majority wanted for deciding checkpoints. Earlier, we noticed how Buterin and the opposite ETH validators might attempt to counter a censorship gentle fork with their very own counter-censorship exhausting fork, whereas slashing the censors within the course of. Even when they succeeded in making a fork, plenty of worth could be destroyed within the course of, each from the slashing and from a lack of belief.
Closing Ideas
On this essay, we checked out how PoS solves the double-spend downside with Gasper, a mixture of checkpoint/slashing guidelines known as Casper, and a “finest block” voting rule known as GHOST. To recap, Gasper divides time into items known as slots, the place every slot can have at most one block, and the slots are grouped into epochs, the place every epoch refers to 1 checkpoint. If a two-thirds majority votes on a checkpoint, it turns into justified, and if two justified checkpoints happen in a row, the primary of these two checkpoints turns into finalized. As soon as a checkpoint turns into finalized, it turns into unimaginable for a parallel chain to be finalized, except one-third of the validators might get slashed.
On this course of we uncovered 5 ideas of PoS:
- PoS makes use of a adverse (penalty-based) incentive construction.
- PoS is a permissioned system.
- PoS has no guidelines.
- PoS depends on subjective reality.
- In PoS, cash is energy.
Every of those ideas has reverse habits in PoW:
- PoW makes use of a constructive (reward-based) incentive system.
- PoW is a permissionless system (anybody can begin or cease mining at any time).
- In PoW, forks which change the principles get ignored.
- PoW depends on goal reality.
- In PoW, miners serve the customers and have little energy themselves.
I imagine everybody ought to attempt to create the type of world that they wish to reside in. If, like me, you wish to reside in a permissionless world the place you’ll be able to have management over your cash, the place exhausting work is rewarded and passive possession is a legal responsibility and the place your cash will retailer its worth far into the longer term with out altering on a whim, then you could wish to think twice concerning the trade-offs between PoW and PoS, and battle in favor of the ideas you wish to reside by.
It is a visitor publish by Scott Sullivan. Opinions expressed are completely their very own and don’t essentially replicate these of BTC Inc. or Bitcoin Journal.