Based on the U.S. Cybersecurity and Infrastructure Safety Company (CISA), whereas quantum computer systems are incapable of breaking public key encryption algorithms, private and non-private entities want to organize for future threats in opposition to cryptography that’s not quantum resistant. Most of at this time’s digital communications, together with cryptocurrencies, leverage public key encryption and CISA believes when “quantum computer systems attain greater ranges of computing energy and pace, they are going to be able to breaking the general public key cryptography algorithms which can be in use at this time.”
US Authorities Warns Nation-States and Personal Corporations Are Actively Pursuing Quantum Computing Strategies That Might Threaten Present Cryptographic Requirements
Cryptocurrencies that leverage up to date encryption methods might be damaged by quantum computer systems sometime, alongside different digital communications like e mail, messaging providers, and on-line banking. That’s based on a latest CISA report revealed on the finish of August. The U.S. authorities entity stresses within the report {that a} transition to post-quantum cryptography is critical. “Don’t wait till the quantum computer systems are in use by our adversaries to behave,” CISA’s report particulars. “Early preparations will guarantee a easy migration to the post-quantum cryptography customary as soon as it’s accessible.”
Discussions about whether or not or not quantum computing will be capable of break public key encryption have been happening since scientists made progress entangling the primary pair of quantum bits (qubits) again in 1998. Quantum computer systems make the most of intricate physics to be able to calculate highly effective equations associated to at this time’s up to date crypto and mathematical techniques. Since 1998, tremendous quantum computer systems have improved with 14 calcium ion qubits entangled in 2011, 16 superconducting qubits in 2018, and 18 entangled qubits in 2018. CISA says quantum computer systems will create new alternatives however the tech additionally results in unfavorable penalties when it comes to encryption safety.
“Nation-states and personal corporations are actively pursuing the capabilities of quantum computer systems,” CISA’s report particulars. “Quantum computing opens up thrilling new prospects; nonetheless, the implications of this new expertise embody threats to the present cryptographic requirements.”
Whereas Researchers Say Bitcoin’s Public Key Expertise Leverages ‘A number of Quantum-Resistant One-Method Hash Capabilities,’ Some Blockchain Initiatives Put together for a Submit-Quantum World
Cryptocurrencies like Bitcoin leverage up to date encryption strategies and it has been stated many instances through the years that there’s a necessity to guard cryptocurrencies with post-quantum encryption. In 2020, when the commercial agency Honeywell revealed it constructed a quantum pc that successfully leverages six efficient qubits, crypto supporters began discussing quantum computer systems’ potential future results on Bitcoin and 256-bit encryption. Some digital foreign money supporters have already began making preparations for a quantum pc encryption-breaking occasion. Cambridge Quantum Computing is within the midst of working with Honeywell on a undertaking that “could be utilized to any blockchain community.”
Regardless of the efforts by cryptographers, some researchers wholeheartedly imagine large-scale quantum computer systems won’t ever come to fruition. Others suppose the timeline is far nearer than folks anticipate and some scientists have stated it might be roughly 5 years from now. The Nationwide Institute of Requirements and Expertise (NIST) thinks 15 years is extra affordable. In the meantime, Ethereum builders have been researching quantum resistance alongside the Hyperledger Basis’s distributed ledger undertaking Ursa. Cryptographers getting ready for a post-quantum world imagine encryption methods like AES-128 and RSA-2048 is not going to present ample safety in opposition to quantum pc assaults.
Andreas Antonopoulos: ‘Satoshi Nakamoto’s Little Genius Design Ingredient Is Not an Accident’
The talk has raged on for years and many individuals suppose the federal government’s warnings and the latest quantum-based technological achievements by Honeywell, Google, Microsoft, and others, are the incentives folks must embrace post-quantum cryptography.
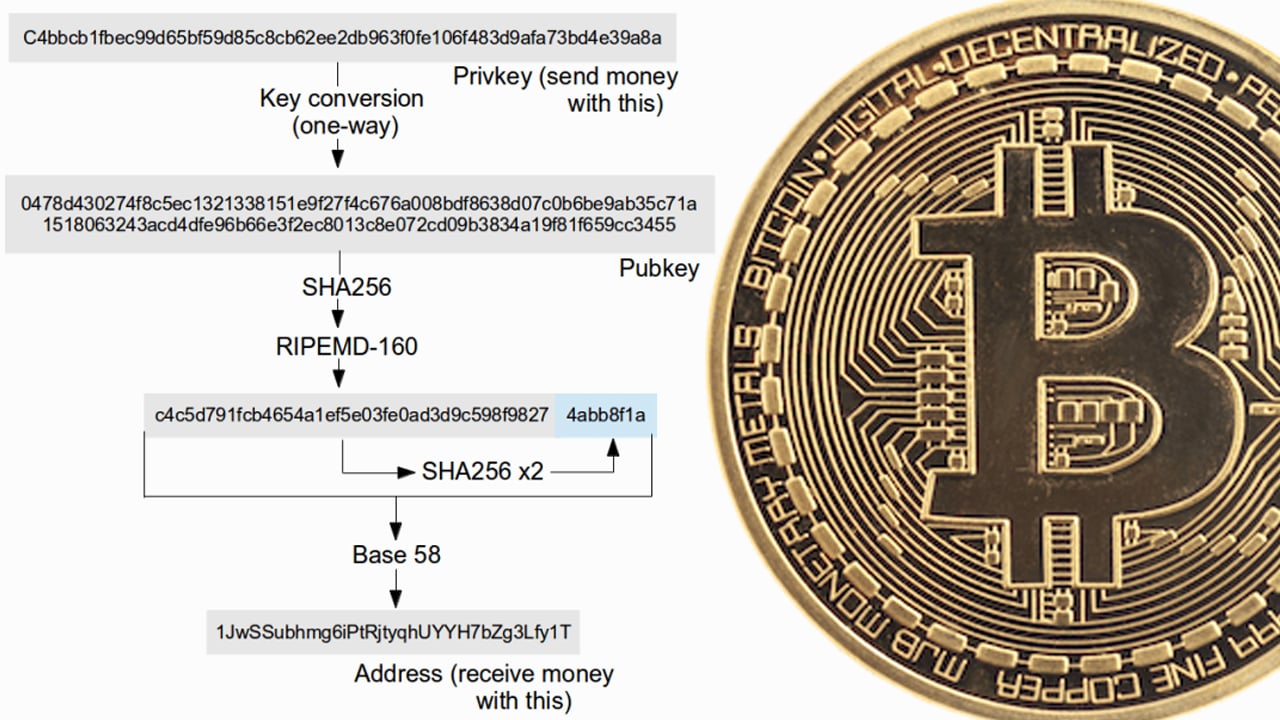
Many articles, analysis studies, and mainstream headlines declare quantum computing will break any up to date encryption and even forecast site visitors jams and accidents nicely earlier than they occur. Nonetheless, Bitcoin proponents have stated on varied events that the SHA256 encryption employed by Satoshi’s creation is a formidable foe in opposition to a post-quantum world.
“In Bitcoin your public key isn’t (initially) made public. When you share your bitcoin tackle with others in order that they will ship you bitcoins, your bitcoin tackle is simply a hash of your public key, not the general public key itself,” software program developer and cryptocurrency proponent Chris Pacia wrote in 2014. “What does that imply in English? A hash perform is a one-way cryptographic perform that takes an enter and turns it right into a cryptographic output. By one-way, I imply which you can’t derive the enter from the output. It’s form of like encrypting one thing [and] then dropping the important thing.”
The software program developer’s 2014 paper on the topic concludes:
All of that could be a difficult approach of claiming that whereas an attacker with a quantum pc might derive the non-public key from the general public key, he couldn’t derive the general public key from the bitcoin tackle because the public key was run by means of a number of quantum-resistant one-way hash capabilities.
In a video that includes the bitcoin evangelist Andreas Antonopoulos, he stated that utilizing totally different bitcoin addresses each time is essential to bitcoin safety. Antonopoulos careworn that Satoshi’s two cryptography design selections are “completely genius.” “What you utilize, which is a Bitcoin tackle, is a double-hashed model of your public key — which implies that the general public key’s by no means seen by anybody till you declare it by spending the transaction … This little genius design component is just not an accident,” Antonopoulos additional stated in his keynote speech. “What it does is, it creates a second layer abstraction of the underlying cryptographic algorithm utilized in elliptic curve digital signatures permitting you to do future upgrades.”
Antonopoulos continued:
Which implies that the previous is safe as a result of it’s hidden behind the second veil of a special algorithm and the long run could be modified as a result of you possibly can current an tackle that’s not the hash of an elliptic curve, or its the hash of a special elliptic curve, or its the hash of an even bigger elliptic curve, or its the hash of a signing algorithm that’s quantum-resistant that has nothing to do with elliptic curve. So, you are able to do forwards modification to safe the long run, and also you’ve bought backwards safety as a result of you could have hid the previous.
Tags on this story
What do you concentrate on the U.S. authorities’s latest warning about quantum computer systems? Tell us what you concentrate on this topic within the feedback part under.
Jamie Redman
Jamie Redman is the Information Lead at Bitcoin.com Information and a monetary tech journalist residing in Florida. Redman has been an lively member of the cryptocurrency neighborhood since 2011. He has a ardour for Bitcoin, open-source code, and decentralized purposes. Since September 2015, Redman has written greater than 6,000 articles for Bitcoin.com Information in regards to the disruptive protocols rising at this time.
Picture Credit: Shutterstock, Pixabay, Wiki Commons, Chris Pacia, Bitcoin Not Bombs,
Disclaimer: This text is for informational functions solely. It’s not a direct supply or solicitation of a suggestion to purchase or promote, or a advice or endorsement of any merchandise, providers, or corporations. Bitcoin.com doesn’t present funding, tax, authorized, or accounting recommendation. Neither the corporate nor the creator is accountable, immediately or not directly, for any harm or loss brought about or alleged to be brought on by or in reference to using or reliance on any content material, items or providers talked about on this article.
